The Key Is Generated As Ka Alice's Password
Purpose: Recovering a missing private key in IIS environment.
For Microsoft II8
(Jump to the solution)
Cause:
Entrust SSL certificates do not include a private key. The private key resides on the server that generated the Certificate Signing Request (CSR). When installed correctly, the Server Certificate will match up with the private key as displayed below:
If the private key is missing, the circled message indicating a good correspondence with private key will be missing as shown here:
- The Key Is Generated As Ka Alice's Password Change
- The Key Is Generated As Ka Alice's Password Free
- The Key Is Generated As Ka Alice's Password Change
- The Key Is Generated As Ka Alice's Password Pdf
- The Key Is Generated As Ka Alice's Password Download
A missing private key could mean:
- The certificate is not being installed on the same server that generated the CSR.
- The pending request was deleted from IIS.
- The certificate was installed through the Certificate Import Wizard rather than through IIS.
In this technote we do not discuss how to determine the reason the private key is missing. Select the link corresponding to each reason listed above for more information.
There's a video for this guide. Watch the video here.
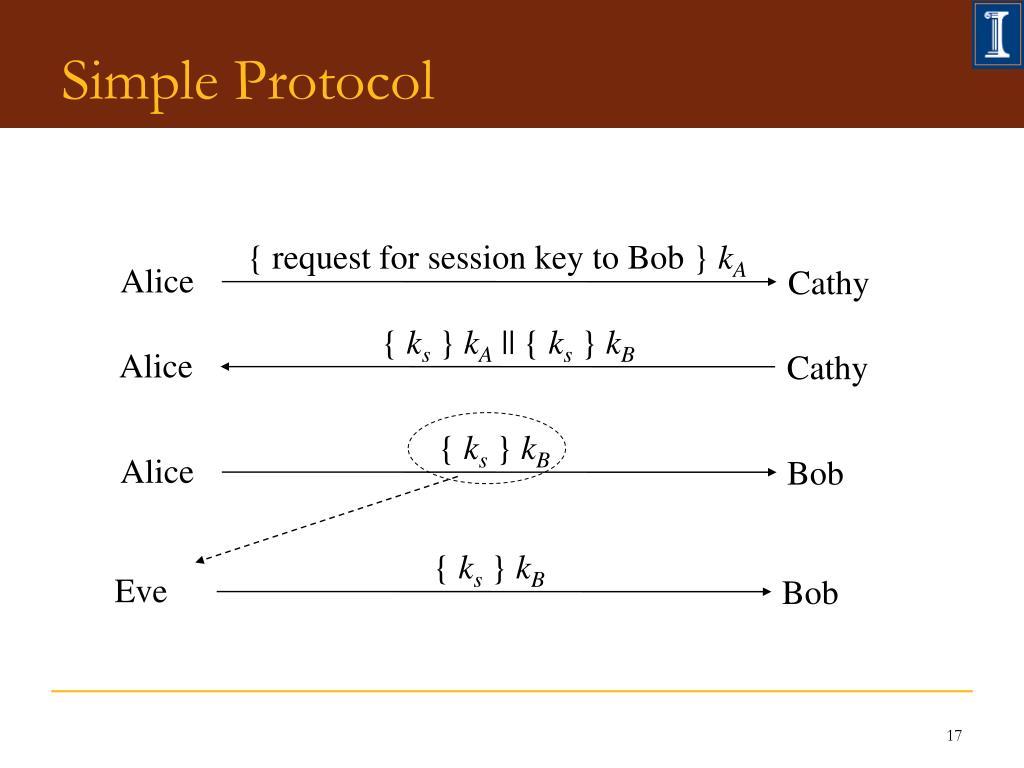
Dec 14, 2013. Since 1Password is unhappy about the previous name of my extension, a.k.a. OnePassword, and threat to sue me in the court. I'm going to rename this to 123 Password. Ciphers Where Alice and Bob Need to Meet Based on notes by William Gasarch We will use three characters: Alice and Bob who want to communicate secretly, and Eve who wants to see what they are talking about. Alice and Bob do not want Eve to be able to decode their messages. The Plaintext is the message you want to send. For example Discrete.
1) Snap-In Configuration
2) Import the Server Certificate
3) Recover the private key
Use the following steps to add the Certificates snap-in:
1. Click Start, and then search for Run.2. Type in mmc and click OK.
3. From the File menu, choose Add/Remove Snap-in.
4. Select Certificates and then Add.
5. Choose the Computer account option and click Next.
6. Select Local Computer and then click Finish.
7. Click Close, and then click OK. The snap-in for Certificates (Local Computer) appears in the console.
Use the following steps to import your Server Certificate into the Personal certificate store. If the Server Certificate has already been imported into the Personal store, you may skip this step.
From the MMC console opened in the above steps:
1. Expand the Certificates (Local Computer) tree in the left preview panel.
2. Right-click Personal and select All Tasks > Import.
3. The Certificate Import Wizard appears. Click Next.
4. Browse to the location of your Server Certificate file and click Next.
5. Select Place all certificates in the following store and click Next.
6. Click Finish to complete the Certificate Import Wizard.
7. A dialog box appears indicating the import was successful. Click OK.Use the following steps to recover your private key using the certutil command.
1. Locate your Server Certificate file by opening Microsoft Internet Information Services Manager, then on the right side select Tools > Internet Information Services (IIS) Manager.
2. Once in IIS Manager, select your server, then on the right side, Server Certificates. You will see all certificates currently on that server. Scroll over the certificate you are trying to install, right click, then select View.
3. There, you can view the certificate information. As you can see, there is no indication of a good correspondence with the private key.
4. Click the Details tab. Write down the serial number of the certificate.
5. We will need to recover the private key using a command prompt. In order to recover the key, we must do so using command prompt as an administrator. To do so, slick Start, then on then open all App. Under Windows System, find Command Prompt. Right click Command prompt and then Run as administrator. Confirm the action and continue.
6. Make sure you are on the right directory in command prompt.
e.g., if your server directory is “c:/users/srv2012_r2_std_x64”, on the command line type “cd c:/users/srv2012_r2_std_x64”. Note that “cd” is the command used to change directories in command prompt.
7. Now that we are in the right place, enter the following command at the prompt: certutil –repairstore my <serial number> where <serial number> is the serial number obtained in Step 2 with spaces removed.
8. If Windows is able to recover the private key, you see the message:
CertUtil: -repairstore command completed successfully.
If your private key was recovered successfully, your Server Certificate installation is complete.
If the private key was not recovered successfully, you will need to generate a new Certificate Signing Request and submit it to Entrust Datacard to have your certificate re-issued, or re-issue the certificate using your ECS Enterprise account.
Check that your Certificate has been successfully installed by testing it on the Entrust SSL Install Checker.
If you have any questions or concerns please contact the Entrust Certificate Services Supportdepartment for further assistance:
Hours of Operation:
Sunday 8:00 PM ET to Friday 8:00 PM ET
North America (toll free): 1-866-267-9297
Outside North America: 1-613-270-2680 (or see the list below)
NOTE: It is very important that international callers dial the UITF format exactly as indicated. Do not dial an extra '1' before the '800' or your call will not be accepted as an UITF toll free call.
Country | Number |
Australia | 0011 - 800-3687-7863 1-800-767-513 |
Austria | 00 - 800-3687-7863 |
Belgium | 00 - 800-3687-7863 |
00 - 800-3687-7863 | |
Finland | 990 - 800-3687-7863 (Telecom Finland) |
France | 00 - 800-3687-7863 |
Germany | 00 - 800-3687-7863 |
Hong Kong | 001 - 800-3687-7863 (Voice) |
Ireland | 00 - 800-3687-7863 |
Israel | 014 - 800-3687-7863 |
Italy | 00 - 800-3687-7863 |
Japan | 001 - 800-3687-7863 (KDD) |
Korea | 001 - 800-3687-7863 (Korea Telecom) |
Malaysia | 00 - 800-3687-7863 |
Netherlands | 00 - 800-3687-7863 |
New Zealand | 00 - 800-3687-7863 0800-4413101 |
Norway | 00 - 800-3687-7863 |
Singapore | 001 - 800-3687-7863 |
Spain | 00 - 800-3687-7863 |
Sweden | 00 - 800-3687-7863 (Telia) |
Switzerland | 00 - 800-3687-7863 |
Taiwan | 00 - 800-3687-7863 |
United Kingdom | 00 - 800-3687-7863 |
S/KEY is a one-time password system developed for authentication to Unix-likeoperating systems, especially from dumb terminals or untrusted public computers on which one does not want to type a long-term password. A user's real password is combined in an offline device with a short set of characters and a decrementing counter to form a single-use password. Because each password is only used once, they are useless to password sniffers.
Because the short set of characters does not change until the counter reaches zero, it is possible to prepare a list of single-use passwords, in order, that can be carried by the user. Alternatively, the user can present the password, characters, and desired counter value to a local calculator to generate the appropriate one-time password that can then be transmitted over the network in the clear. The latter form is more common and practically amounts to challenge–response authentication.
S/KEY is supported in Linux (via pluggable authentication modules), OpenBSD, NetBSD, and FreeBSD, and a generic open-source implementation can be used to enable its use on other systems. OpenSSH also implement S/KEY since version OpenSSH 1.2.2 released in December 1, 1999[1]. One common implementation is called OPIE. S/KEY is a trademark of Telcordia Technologies, formerly known as Bell Communications Research (Bellcore).
S/KEY is also sometimes referred to as Lamport's scheme, after its author, Leslie Lamport. It was developed by Neil Haller, Phil Karn and John Walden at Bellcore in the late 1980s. With the expiration of the basic patents onpublic-key cryptography and the widespread use of laptop computers running SSH andother cryptographic protocols that can secure an entire session, not just the password, S/KEY is fallinginto disuse.[citation needed] Schemes that implement two-factor authentication, by comparison, are growing in use.[2]
Password generation[edit]
The server is the computer that will perform the authentication.
- This step begins with a secret key W. This secret can either be provided by the user, or can be generated by a computer. Either way, if this secret is disclosed, then the security of S/KEY is compromised.
- A cryptographic hash functionH is applied n times to W, thereby producing a hash chain of n one-time passwords. The passwords are the results of the application of the cryptographic hash function:
- H(W), H(H(W)), .., Hn(W).
- The initial secret W is discarded.
- The user is provided with the n passwords, printed out in reverse order:
- Hn(W), Hn−1(W), .., H(H(W)), H(W).
- The passwords H(W), H(H(W)), .., Hn−1(W) are discarded from the server. Only the password Hn(W), the one at the top of the user's list, is stored on the server.
Authentication[edit]
After password generation, the user has a sheet of paper with n passwords on it.
More ideally, though perhaps less commonly in practice, the user may carry a small, portable, secure, non-networked computing device capable of regenerating any needed password given the secret passphrase, the salt, and the number of iterations of the hash required, the latter two of which are conveniently provided by the server requesting authentication for login.
In any case, the first password will be the same password that the server has stored. This first password will not be used for authentication (the user should scratch this password on the sheet of paper), the second one will be used instead:
- The user provides the server with the second password pwd on the list and scratches that password.
- The server attempts to compute H(pwd), where pwd is the password supplied. If H(pwd) produces the first password (the one the server has stored), then the authentication is successful. The server will then store pwd as the current reference.
The Key Is Generated As Ka Alice's Password Change
For subsequent authentications, the user will provide passwordi. (The last password on the printed list, passwordn, is the first password generated by the server, H(W), where W is the initial secret).The server will compute H(passwordi) and will compare the result to passwordi−1, which is stored as reference on the server.
Security[edit]
The security of S/KEY relies on the difficulty of reversing cryptographic hash functions. Assume an attacker manages to get hold of a password that was used for a successful authentication. Supposing this is passwordi, this password is already useless for subsequent authentications, because each password can only be used once. It would be interesting for the attacker to find out passwordi−1, because this password is the one that will be used for the next authentication.
However, this would require inverting the hash function that produced passwordi−1 using passwordi (H(passwordi−1) = passwordi), which is extremely difficult to do with current cryptographic hash functions.

Nevertheless, S/KEY is vulnerable to a man in the middle attack if used by itself. It is also vulnerable to certain race conditions, such as where an attacker's software sniffs the network to learn the first N − 1 characters in the password (where N equals the password length), establishes its own TCP session to the server, and in rapid succession tries all valid characters in the N-th position until one succeeds. These types of vulnerabilities can be avoided by using ssh, SSL, SPKM, or other encrypted transport layer.
Since each iteration of S/KEY doesn't include the salt or count, it is feasible to find collisions directly without breaking the initial password. This has a complexity of 264, which can be pre-calculated with the same amount of space. The space complexity can be optimized by storing chains of values, although collisions might reduce the coverage of this method, especially for long chains.[3]
Someone with access to an S/KEY database can break all of them in parallel with a complexity of 264. While they wouldn't get the original password, they would be able to find valid credentials for each user. In this regard, it is similar to storing unsalted 64-bit hashes of strong, unique passwords.
The Key Is Generated As Ka Alice's Password Free
The S/KEY protocol can loop. If such a loop were created in the S/KEY chain, an attacker could use user's key without finding the original value, and possibly without tipping off the valid user. The pathological case of this would be an OTP that hashes to itself.
The Key Is Generated As Ka Alice's Password Change
Usability[edit]
Internally, S/KEY uses 64-bit numbers. For human usability purposes, each number is mapped to six short words, of one to four characters each, from a publicly accessible 2048-word dictionary. For example, one 64-bit number maps to 'ROY HURT SKI FAIL GRIM KNEE'.[4]
See also[edit]
- PGP biometric word list uses two lists of 256 words, each word representing 8 bits.
References[edit]
The Key Is Generated As Ka Alice's Password Pdf
- ^'OpenSSH Project History'. OpenSSH. Retrieved 2019-12-05.
- ^'Global Multi-factor Authentication Market 2017-2021'. TechNavio. August 2017. Retrieved 2019-12-05.
- ^Samuel, Michael (2011-07-01). 'S/Key Dungeon Attack'. Retrieved 2019-12-05.
- ^Haller, Neil; Metz, Craig; Nesser II, Philip J.; Straw, Mike. 'Appendix D: Dictionary for Converting Between 6-Word and Binary Formats'. A One-Time Password System. IETF.
External links[edit]
- The S/KEY One-Time Password System (RFC 1760)
- A One-Time Password System (RFC 2289)