Python Crypto Rsa Key Generate
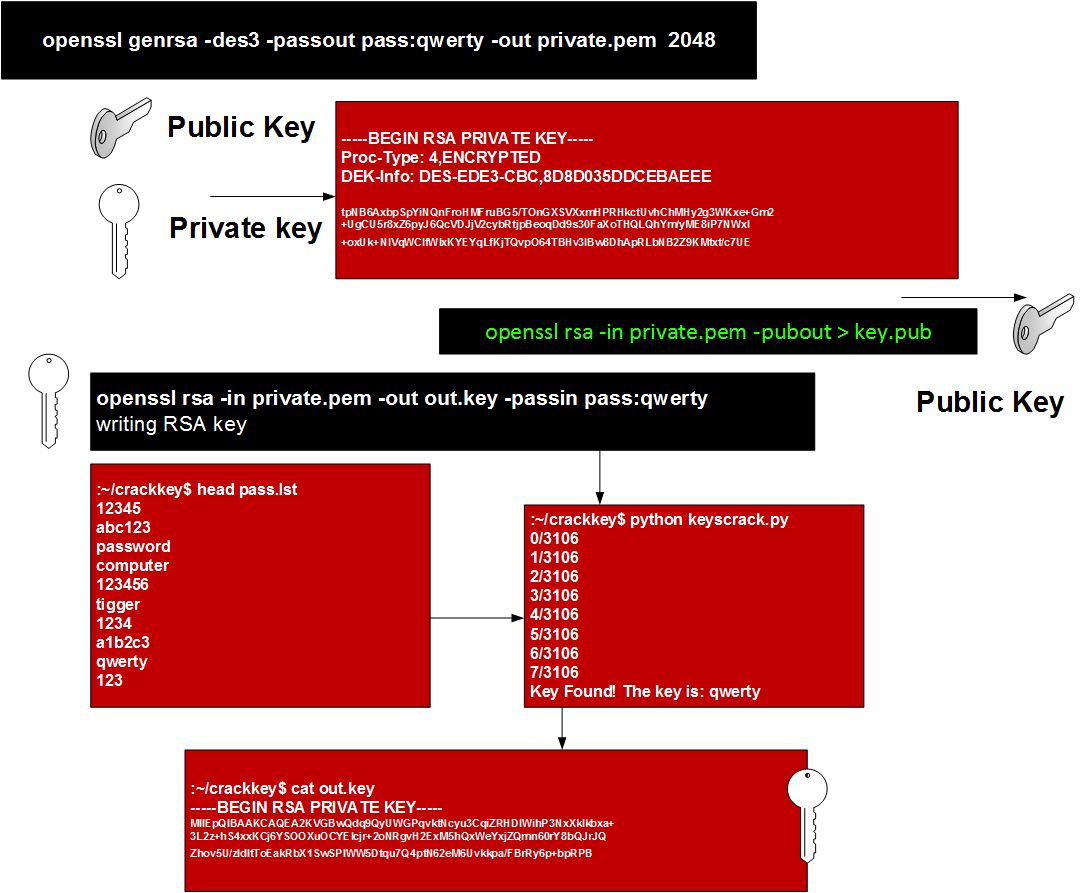
Generate an RSA key¶ The following code generates a new RSA key pair (secret) and saves it into a file, protected by a password. We use the scrypt key derivation function to thwart dictionary attacks. At the end, the code prints our the RSA public key in ASCII/PEM format.
- I need help using RSA encryption and decryption in Python. I am creating a private/public key pair, encrypting a message with keys and writing message to a file. Then I am reading ciphertext from.
- Dec 21, 2017 Black Hat Python — Encrypt and Decrypt with RSA Cryptography. Its very straighforward to encrypt/ decrypt files using Python. In this post, I will show a few scripts to accomplish this.
- Let's demonstrate in practice the RSA sign / verify algorithm. We shall use the pycryptodome package in Python to generate RSA keys.After the keys are generated, we shall compute RSA digital signatures and verify signatures by a simple modular exponentiation (by encrypting and decrypting the message hash).
- Crypto — Generic cryptographic module. Check the consistency of an RSA private key. This is the Python equivalent of OpenSSL’s RSAcheckkey. Returns: True if key is consistent. Generate a key pair of the given type, with the given number of bits.
RSA is the most widespread and used public key algorithm. Its security isbased on the difficulty of factoring large integers. The algorithm haswithstood attacks for more than 30 years, and it is therefore consideredreasonably secure for new designs.
The algorithm can be used for both confidentiality (encryption) andauthentication (digital signature). It is worth noting that signing anddecryption are significantly slower than verification and encryption.
The cryptographic strength is primarily linked to the length of the RSA modulus n.In 2017, a sufficient length is deemed to be 2048 bits. For more information,see the most recent ECRYPT report.
Both RSA ciphertexts and RSA signatures are as large as the RSA modulus n (256bytes if n is 2048 bit long).
The module Crypto.PublicKey.RSA provides facilities for generating new RSA keys,reconstructing them from known components, exporting them, and importing them.
As an example, this is how you generate a new RSA key pair, save it in a filecalled mykey.pem, and then read it back:
Crypto.PublicKey.RSA.generate(bits, randfunc=None, e=65537)¶Create a new RSA key pair.
The algorithm closely follows NIST FIPS 186-4 in itssections B.3.1 and B.3.3. The modulus is the product oftwo non-strong probable primes.Each prime passes a suitable number of Miller-Rabin testswith random bases and a single Lucas test.
| Parameters: |
|
|---|
Returns: an RSA key object (RsaKey, with private key).
Crypto.PublicKey.RSA.construct(rsa_components, consistency_check=True)¶Construct an RSA key from a tuple of valid RSA components.
The modulus n must be the product of two primes.The public exponent e must be odd and larger than 1.
In case of a private key, the following equations must apply:
| Parameters: |
|
|---|---|
| Raises: |
|
Returns: An RSA key object (RsaKey).
Crypto.PublicKey.RSA.import_key(extern_key, passphrase=None)¶Import an RSA key (public or private).
| Parameters: |
|
|---|
Returns: An RSA key object (RsaKey).
| Raises: | ValueError/IndexError/TypeError – When the given key cannot be parsed (possibly because the passphrase is wrong). |
|---|
Crypto.PublicKey.RSA.RsaKey(**kwargs)¶Class defining an actual RSA key.Do not instantiate directly.Use generate(), construct() or import_key() instead.
| Variables: |
|
|---|
exportKey(format='PEM', passphrase=None, pkcs=1, protection=None, randfunc=None)¶Export this RSA key.
| Parameters: |
|
|---|---|
| Returns: | the encoded key |
| Return type: | byte string |
| Raises: |
|
Warning
If you don’t provide a pass phrase, the private key will beexported in the clear!
export_key(format='PEM', passphrase=None, pkcs=1, protection=None, randfunc=None)¶Export this RSA key.
| Parameters: |
|
|---|---|
| Returns: | the encoded key |
| Return type: | byte string |
| Raises: |
|
Warning
If you don’t provide a pass phrase, the private key will beexported in the clear!
has_private()¶Whether this is an RSA private key
publickey()¶A matching RSA public key.
| Returns: | a new RsaKey object |
|---|
size_in_bits()¶Size of the RSA modulus in bits Battlefield 4 premium key generator.
size_in_bytes()¶The minimal amount of bytes that can hold the RSA modulus
Generate Crypto Key Rsa Cisco
Crypto.PublicKey.RSA.oid = '1.2.840.113549.1.1.1'¶Object ID for the RSA encryption algorithm. /generate-product-key-for-microsoft-office-2007.html. This OID often indicatesa generic RSA key, even when such key will be actually used for digitalsignatures.
Encrypt data with AES¶
The following code generates a new AES128 key and encrypts a piece of data into a file.We use the EAX mode because it allows the receiver to detect anyunauthorized modification (similarly, we could have used other authenticatedencryption modes like GCM, CCM or SIV).
At the other end, the receiver can securely load the piece of data back (if they know the key!).Note that the code generates a ValueError exception when tampering is detected.
Generate an RSA key¶
The following code generates a new RSA key pair (secret) and saves it into a file, protected by a password.We use the scrypt key derivation function to thwart dictionary attacks.At the end, the code prints our the RSA public key in ASCII/PEM format:
The following code reads the private RSA key back in, and then prints again the public key:
Generate public key and private key¶
The following code generates public key stored in receiver.pem and private key stored in private.pem. These files will be used in the examples below. Every time, it generates different public key and private key pair.
Encrypt data with RSA¶
The following code encrypts a piece of data for a receiver we have the RSA public key of.The RSA public key is stored in a file called receiver.pem.
Since we want to be able to encrypt an arbitrary amount of data, we use a hybrid encryption scheme.We use RSA with PKCS#1 OAEP for asymmetric encryption of an AES session key.The session key can then be used to encrypt all the actual data.
Generate Crypto Key Cisco
As in the first example, we use the EAX mode to allow detection of unauthorized modifications.
Python Crypto Generate Rsa Key Pair
The receiver has the private RSA key. They will use it to decrypt the session keyfirst, and with that the rest of the file: