Generate Public Key Mac -----begin-public-key---
You generate an SSH key through macOS by using the Terminal application. Once you upload a valid public SSH key, the Triton Compute Service uses SmartLogin to copy the public key to any new SmartMachine you provision.
SiteGround uses key pairs for SSH authentication purposes, as opposed to plain username and password. More information on SSH keys is available here. You can generate an SSH key pair in Mac OS following these steps: Open up the Terminal by going to Applications - Utilities - Terminal. A separate public key file is not created at the same step though. To extract public key from the private key file into separate public key file you use your openssl rsa -in private.pem -pubout -out public.pem command. When you produce a public key this way, it is extracted from the private key file, not calculated. Save both your private and public keys to your computer (simply copy & paste the keys to a text editor such as Notepad and save the file). If you lose either key, you will be unable to send encrypted messages nor decrypt any received message. Once you have saved both keys, you may wish to try to encrypt a message using PGP.
- Generating Your SSH Public Key. Many Git servers authenticate using SSH public keys. In order to provide a public key, each user in your system must generate one if they don’t already have one. This process is similar across all operating systems. First, you should check to make sure you don’t already have a key.
- Apr 12, 2018 SSH-key-based authentication provides a more secure alternative to password-based authentication. In this tutorial we'll learn how to set up SSH key-based authentication on an Ubuntu 16.04 installation.
- Supported SSH key formats. Azure currently supports SSH protocol 2 (SSH-2) RSA public-private key pairs with a minimum length of 2048 bits. Other key formats such as ED25519 and ECDSA are not supported. Create an SSH key pair. Use the ssh-keygen command to generate SSH public and private key files. By default, these files are created in the.
- Setting up public key authentication Generate an SSH Key Copy the key to a server Test the new key Troubleshooting How ssh-copy-id works Some best practices for SSH keys Use a passphrase when possible Add a command restriction when possible Managing SSH keys Command-line options Ssh-copy-id on Mac Installation using Homebrew Installation from.
Joyent recommends RSA keys because the node-manta CLI programs work with RSA keys both locally and with the ssh agent. DSA keys will work only if the private key is on the same system as the CLI, and not password-protected.
About Terminal
Terminal is the terminal emulator which provides a text-based command line interface to the Unix shell of macOS.
To open the macOS Terminal, follow these steps:
- In Finder, choose Utilities from the Applications folder.
- Find Terminal in the Utilities listw.
- Open Terminal.
The Terminal window opens with the commandline prompt displaying the name of your machine and your username.
Generating an SSH key
An SSH key consists of a pair of files. One is the private key, which should never be shared with anyone. The other is the public key. The other file is a public key which allows you to log into the containers and VMs you provision. When you generate the keys, you will use ssh-keygen to store the keys in a safe location so you can bypass the login prompt when connecting to your instances.
To generate SSH keys in macOS, follow these steps:
Enter the following command in the Terminal window.
This starts the key generation process. When you execute this command, the
ssh-keygenutility prompts you to indicate where to store the key.Press the ENTER key to accept the default location. The
ssh-keygenutility prompts you for a passphrase.- Type in a passphrase. You can also hit the ENTER key to accept the default (no passphrase). However, this is not recommended.
You will need to enter the passphrase a second time to continue. /ea-serial-key-generator-free-download.html.
After you confirm the passphrase, the system generates the key pair.
Your private key is saved to the id_rsa file in the .ssh directory and is used to verify the public key you use belongs to the same Triton Compute Service account.
| Never share your private key with anyone! |
|---|
Your public key is saved to the id_rsa.pub;file and is the key you upload to your Triton Compute Service account. You can save this key to the clipboard by running this:
Importing your SSH key
Now you must import the copied SSH key to the portal.
- After you copy the SSH key to the clipboard, return to your account page.
- Choose to Import Public Key and paste your SSH key into the Public Key field.
- In the Key Name field, provide a name for the key. Note: although providing a key name is optional, it is a best practice for ease of managing multiple SSH keys.
- Add the key. It will now appear in your table of keys under SSH.
Troubleshooting
You may see a password prompt like this:
This is because:
- You did not enter the correct passphrase.
- The private key on your Macintosh (
id_rsa) does not match the public key stored with your Triton Compute Service account. - The public key was not entered correctly in your Triton account.
What are my next steps?
Right in the portal, you can easily create Docker containers, infrastructure containers, and hardware virtual machines.
In order to use the Terminal to create instances, set up triton and CloudAPI as well as the triton-docker commandline tool.
This guide will show you how to enable SSH (remote login) on your Mac OS X machine and connect to it using a private key file (.ppk) while disabling password logins (more secure). In this example, we will setup the remote connection using Putty.
- Enable SSH on your Mac. Go to System Preferences -> Sharing -> Remote Login.
- Now, we will generate our private and public SSH keys on our Mac. Open Terminal and type the following commands.
Create a .ssh directory. This directory will be hidden in your Mac X User home path.
Generate SSH private and public keys.
- Now, we want to create an authorized_keys file in the same directory to allow remote hosts to connect to our Mac using the key file we just generated.
Create the authorized_keys file in Terminal.

- Let’s take a look at the keys and authorized keys files we just created. At the menu bar, select Go -> Go to Folder… and type /Users/USER/.ssh replacing USER with your Mac X username. We see 3 files.
authorized_keys - your shared public key file
id_rsa - your private key
id_rsa.pub - your public key
- We want to copy our Public Key exactly into our authorized_keys file. Open id_rsa.pub and copy the text into your authorized_keys file. Save the file. (To do this, you can drag both files to your Desktop to gain access to perform the copies if needed, then drag back to the .ssh folder). See example below.
- In order to use Putty to connect via SSH via a private key, we must convert the id_rsa private key to Putty format (.ppk). We will use PuttyGen.exe to convert our id_rsa private key to a .ppk file. Download and install PuttyGen here.
Note:You can run PuttyGen.exe on Mac OS X following this guide. Otherwise, you will need to run PuttyGen on a Windows machine.
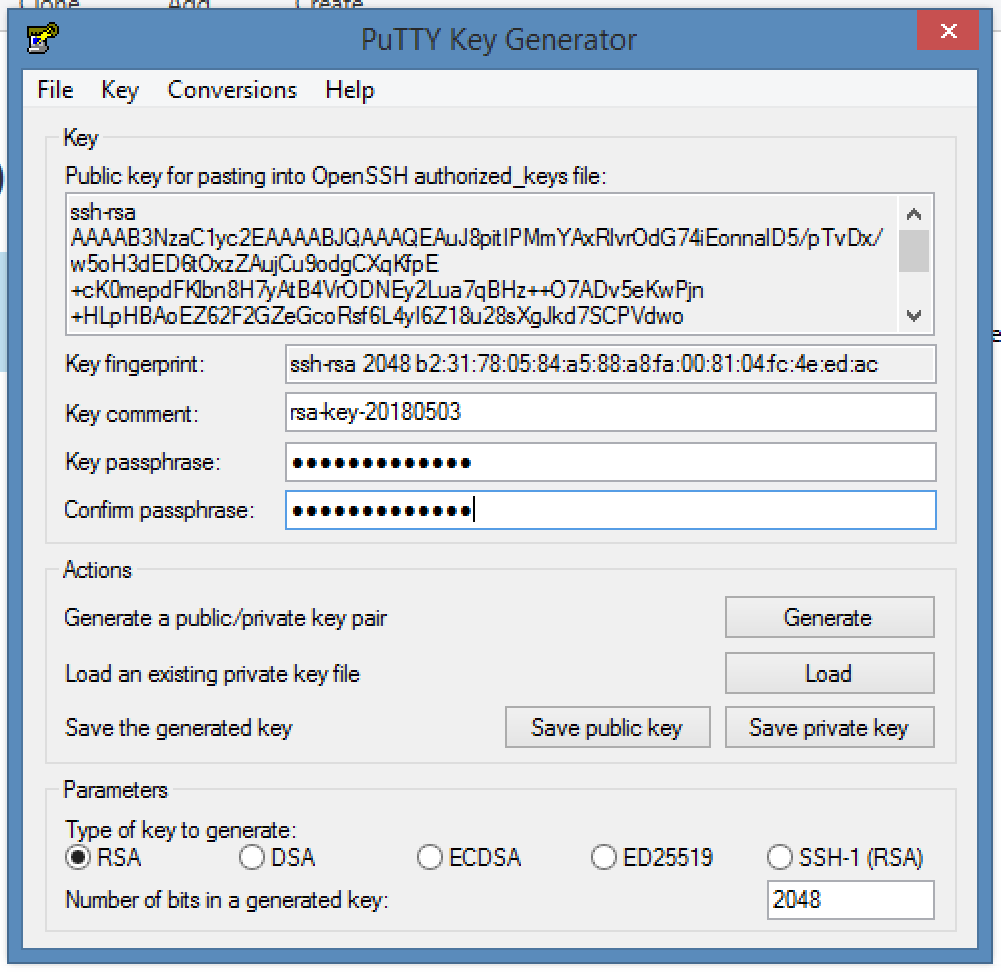
- Launch PuttyGen.exe and click Load.
- For Files of Type select All Files. Locate and select your id_rsa private key.
- Click Save private key. Click Yes to save without a password (this is not needed). You can name the file whatever you want.
You now have a .ppk file we can use for our Putty connection. Save this key somewhere safe and never share it with anyone!
Next, we will configure SSH on our Mac to only allow key authentications and disable password authentications. This will immediately drop a connection made to our Mac unless a key file is being used (more secure).
Configure SSH on Mac OS X to Force Private Key Authentication Only
- At the menu bar, select Go -> Go to Folder… and type /etc/ssh/ and hit return.
- Open the sshd_config file. (To edit this, file you can drag it to your Desktop to edit then drag back to same folder)
- We need to change 2 lines in sshd_config file.
Change UsePAM no
Uncomment and change PasswordAuthentication no
- Save the ssh_config file.
- Restart Mac X remote login for our changes to take affect. Go to System Preferences -> Sharing -> Remote Login and turn off / on.
Now, we can use Putty to create an SSH connection to our Mac we generated our keys on. Download and install Putty here.
Symmetric Key
Note:You can run Putty.exe on Mac OS X following this guide.
Open Putty and create a new connection. We will point to our private key file (.ppk). Go to Connection -> SSH -> Auth and load the .ppk file here. This can be tricky, ensure your creating a new connection in Putty and saving it so it remembers the key we just imported.
Try connecting. You will receive a login prompt for username. This will be the user of your Mac (any other username you put here will fail immediately).
If successful, you will login to your shell immediately pictured below! No password needed!
Secret Key
Please use the comment form to report dead links.