Flask Sesshion Secret_key Generator
Session data is stored at the top of the cookie, and the server signs it in encrypted mode.For this encryption, the Flask application requires a defined SECRETKEY. Related course: Python Flask: Create Web Apps with Flask. Session Session object. A Session object is also a dictionary object that contains key value pairs for session variables. The only real difference between cookies and the client-based session is that Flask guarantees that the contents of the session cookie is not tempered by the user (unless he has the secret key). If you want to use server-side sessions in Flask, you can either write your own session interface or use extensions like Flask-Session and Flask-KVSession. Mar 12, 2012 How to generate a secret key with Python. /free-product-key-generator-for-windows-81.html. The crew cd key generator. GitHub Gist: instantly share code, notes, and snippets. Jul 12, 2014 In Part 11 of this series on Flask, we'll look at how to generate a random string for our app's secret key. Code - https://github.com/realpython/flask-intro. How to generate a secret key with Python. GitHub Gist: instantly share code, notes, and snippets.
- Flask Session Secret_key Generator Parts
- Python Flask Secret Key
- Flask Session Secret_key Generator Download
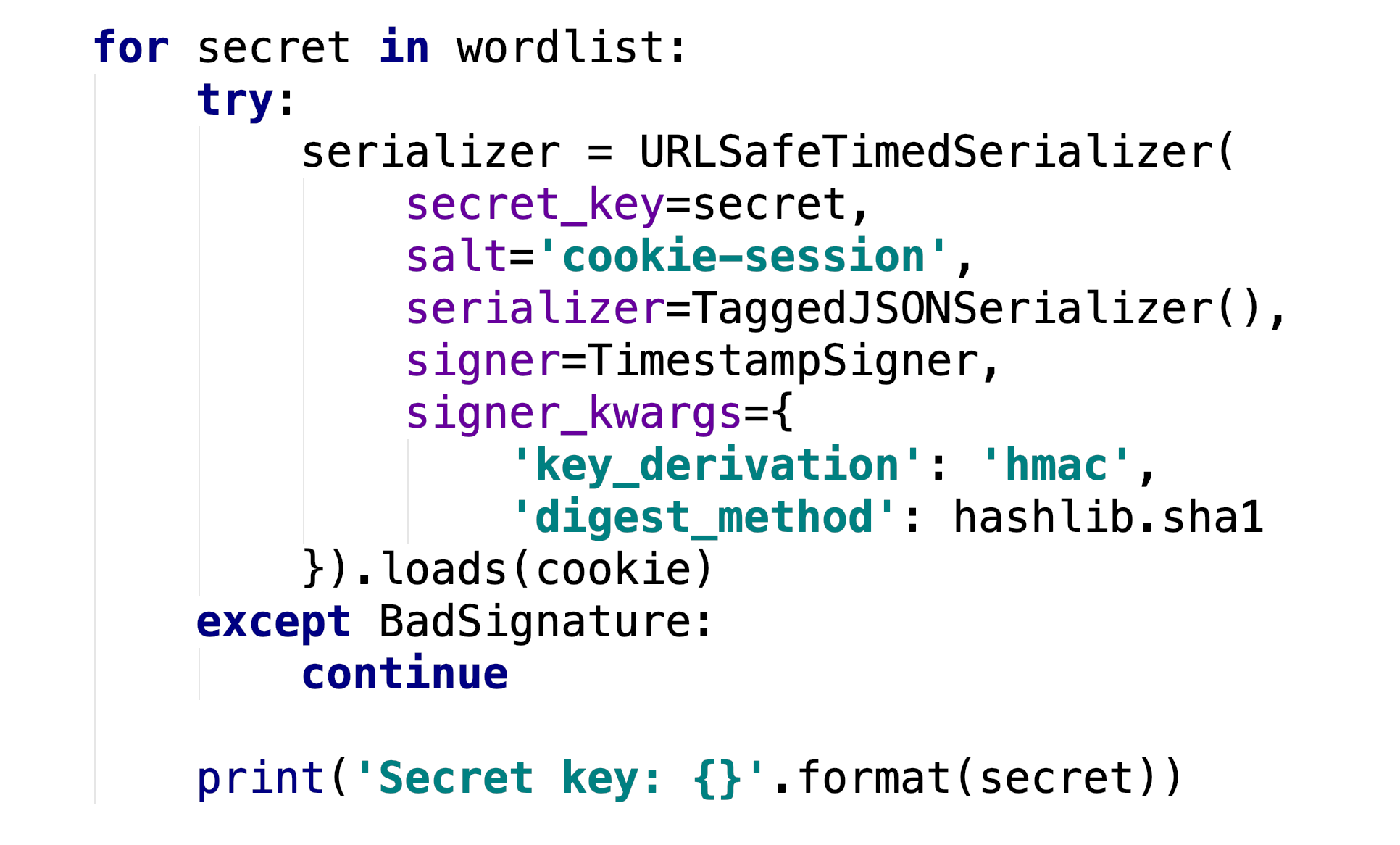
Flask Session Secret_key Generator Parts
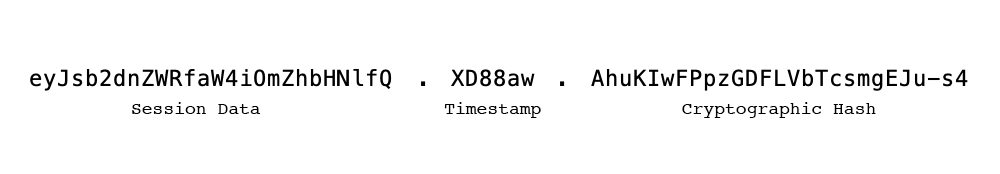
Python Flask Secret Key
| #!/usr/bin/env python |
| # encoding: utf-8 |
| '' |
| generate_keys.py |
| Generate CSRF and Session keys, output to secret_keys.py file |
| Usage: |
| generate_keys.py [-f] |
| Outputs secret_keys.py file in current folder |
| By default, an existing secret_keys file will not be replaced. |
| Use the '-f' flag to force the new keys to be written to the file |
| '' |
| importstring |
| importos.path |
| fromoptparseimportOptionParser |
| fromrandomimportchoice |
| fromstringimportTemplate |
| # File settings |
| file_name='secret_keys.py' |
| file_path=os.path.join( |
| os.path.dirname(os.path.realpath(__file__)), file_name) |
| file_template=Template(''# CSRF- and Session keys |
| CSRF_SECRET_KEY = '$csrf_key' |
| SESSION_KEY = '$session_key' |
| '') |
| # Get options from command line |
| parser=OptionParser() |
| parser.add_option( |
| '-d', |
| '--dir', |
| dest='dir', |
| help='specify dir to output to') |
| parser.add_option( |
| '-f', |
| '--force', |
| dest='force', |
| help='force overwrite of existing secret_keys file', |
| action='store_true') |
| parser.add_option( |
| '-r', |
| '--randomness', |
| dest='randomness', |
| help='length (randomness) of generated key; default = 24', |
| default=24) |
| (options, args) =parser.parse_args() |
| defgenerate_randomkey(length): |
| ''Generate random key, given a number of characters'' |
| chars=string.letters+string.digits |
| return'.join([choice(chars) foriinrange(length)]) |
| defwrite_file(contents): |
| ifoptions.dirisnotNone: |
| file_path=os.path.join(os.path.dirname( |
| os.path.realpath(__file__)), |
| options.dir, |
| file_name) |
| withopen(file_path, 'wb') asf: |
| f.write(contents) |
| defgenerate_keyfile(csrf_key, session_key): |
| ''Generate random keys for CSRF- and session key'' |
| output=file_template.safe_substitute(dict( |
| csrf_key=csrf_key, session_key=session_key |
| )) |
| ifos.path.exists(file_path): |
| ifoptions.forceisNone: |
| print('Warning: secret_keys.py file exists. ') |
| print('Use 'generate_keys.py --force' to force overwrite.') |
| else: |
| write_file(output) |
| else: |
| write_file(output) |
| defmain(): |
| r=options.randomness |
| csrf_key=generate_randomkey(r) |
| session_key=generate_randomkey(r) |
| generate_keyfile(csrf_key, session_key) |
| if__name__'__main__': |
| main() |